Business leaders are worried about the threat posed by cyber-criminals to their organizations, but not as worried as they are about rogue actors, according to a study conducted by IBM’s Institute for Business Value.
IBM surveyed C-suite employeess from 28 different countries and 18 different industries on cybersecurity in the enterprise, and they purposely chose not to include chief information security officers. The results point to a typical C-suite that is aware of the potential cybersecurity threat posed against their organization, but a poor grasp on the main adversaries to defend against. While two-thirds of executives say cybersecurity is “a top concern that must be addressed,” 70 per cent name rogue individuals as posing among the highest threats, with organized crime groups and industry competitors being viewed as the second and third most significant threats.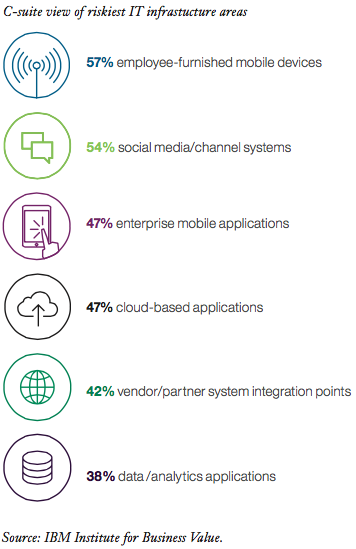
Here’s where some security chiefs might have their work cut out for them. It’s possible that business executives still have the idea of the mythical, lone wolf hacker that we saw in the ’90s and early 2000s. But things have changed a lot since when Mafiaboy made headlines. If company security strategies are too focused on combating random outsider individuals, they could open new vulnerabilities.
The best place to start looking for cybersecurity threats? Inside your own organization. IBM’s Cybersecurity Intelligence Index report shows that 31.5 per cent of data breaches are attributable to malicious insiders and 23.5 per cent to insider errors or failure to follow processes and policies. Yet less than one-third of executives ranked current or former employees in their top three threats.
On the other hand, executives are often mistrusting of technology infrastructure in the hands of employees when it’s legacy infrastructure that more often poses a threat. While 57 per cent of those surveyed say that employee mobile devices pose the greatest cybersecurity risk, the number of mobile security incidents is still small when compared against legacy vulnerabilities. Legacy infrastructure can pose risks especially if new updates are not applied and employees aren’t aware of potential vulnerabilities.
To avoid misunderstandings like this in your own organization, IBM recommends having a CISO who acts as the “captain” in a security team that also includes business executives. Improve the amount of information sharing and collaboration both internally and externally to make sure everyone’s on the same page. Then you’ll have a real chance of defending against cybersecurity threats – no matter where they’re coming from.
